Serving tech enthusiasts for over 25 years.
TechSpot means tech analysis and advice you can trust.
TL;DR: WeChat messages and conversations are not encrypted end-to-end, meaning the app's servers can decrypt and read every message. However, users of the popular messaging app might be concerned to learn that there are vulnerabilities in the encryption protocol that could leave the service open to attack, according to a new study.
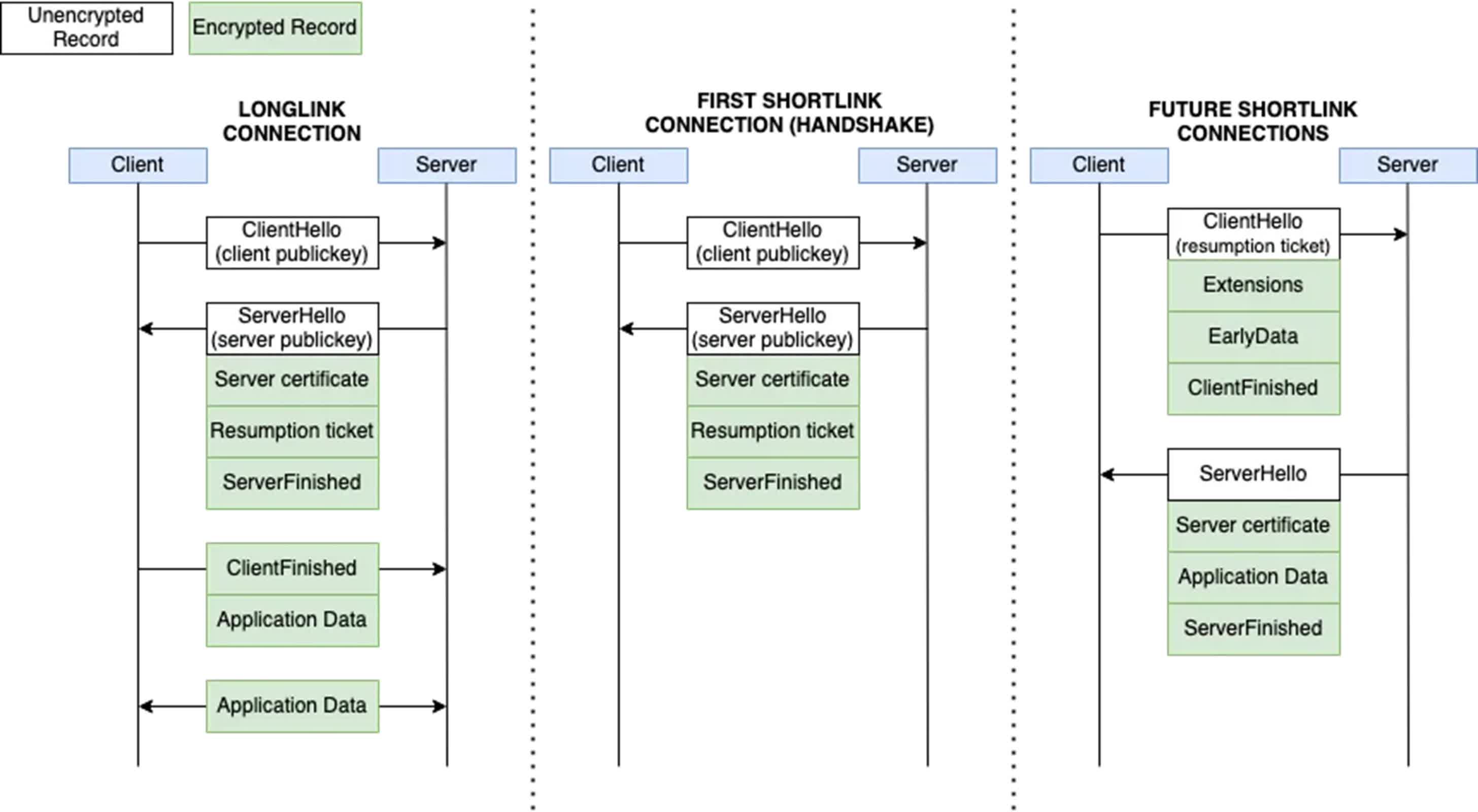
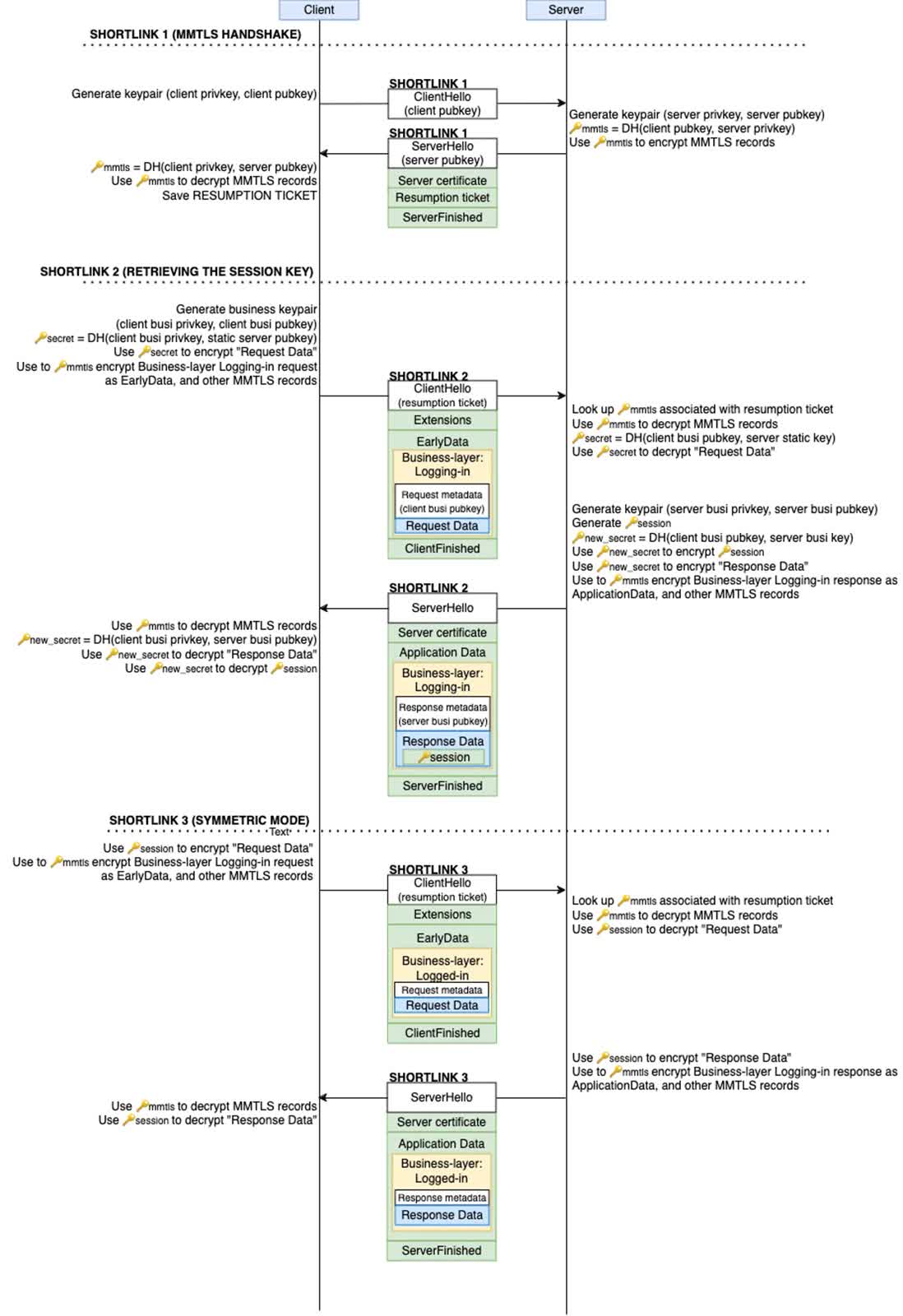
A recent investigation by the University of Toronto's Citizen Lab has uncovered potential security weaknesses in WeChat's custom encryption protocol. These weaknesses arise because the developers of WeChat, which boasts over a billion monthly active users, have modified the Transport Layer Security (TLS) 1.3 protocol, creating a version called MMTLS.
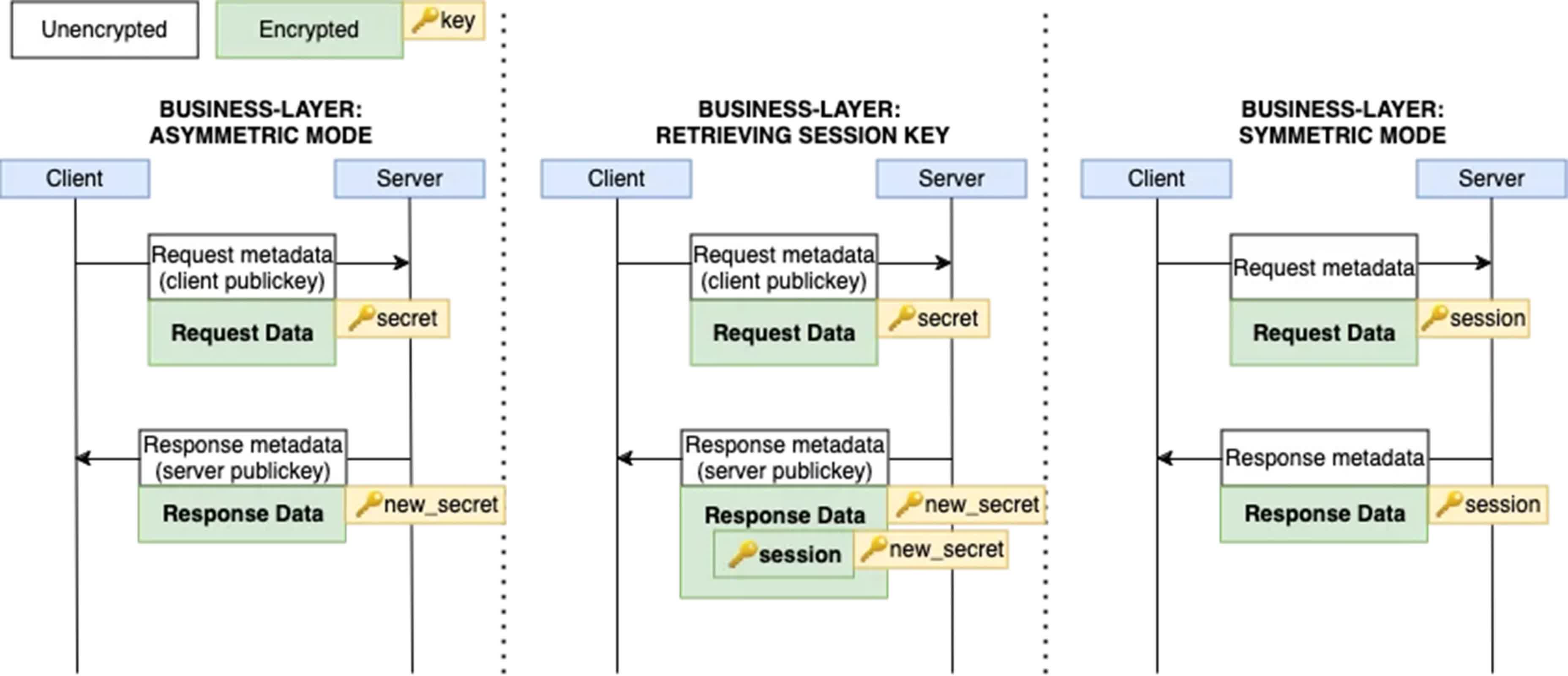
WeChat uses a two-layer encryption system. First, the inner layer, known as "Business-layer encryption," encrypts the plaintext content. This encrypted content is then further encrypted with MMTLS before being transmitted.
While this dual-layer encryption offers some protection, several concerning issues were identified. The Business-layer encryption fails to secure sensitive metadata, such as user IDs and request URIs. Additionally, MMTLS uses deterministic initialization vectors (IVs), which contradict modern cryptographic best practices. Furthermore, the encryption lacks forward secrecy, a crucial feature for long-term security.
Before 2016, WeChat relied solely on Business-layer encryption for network requests. The introduction of MMTLS appears to be an attempt to address the shortcomings of the previous system.
To some extent, this has been effective. The researchers were unable to successfully attack WeChat's encryption in this study because the vulnerable Business-layer encryption is now protected by the MMTLS layer. In earlier versions of WeChat, which lacked MMTLS, the Business-layer encryption was exposed and potentially susceptible to certain attacks. The addition of MMTLS has significantly improved WeChat's overall security by shielding the inner encryption layer from direct attacks.
Nevertheless, the researchers noted that WeChat's implementation falls short of the cryptographic standards expected for an app of its scale. Additionally, other "minor" issues identified by the researchers are not present in the standard, unmodified version of TLS.
The researchers also pointed out that it is a unique practice in China for security developers to create their own custom cryptographic systems rather than using established standards. These homegrown solutions often do not match the effectiveness of widely used protocols like TLS 1.3 or QUIC. Citizen Lab described this as "a growing, concerning trend unique to the Chinese security landscape."
For instance, some Chinese apps implement custom domain resolution methods to combat DNS hijacking by ISPs. Additionally, many Chinese apps, including WeChat, use open-source infrastructure components like Tencent Mars, which may lack proper documentation and security guidance.
Perhaps not surprisingly, the key recommendation by Citizen Lab researchers was that WeChat's parent company Tencent adopt standard TLS or a combination of QUIC and TLS to enhance app security.






:quality(85):upscale()/2024/10/31/831/n/49351773/b7bf33836723d2f0643c55.51137847_.jpg)


 English (US) ·
English (US) ·