Serving tech enthusiasts for over 25 years.
TechSpot means tech analysis and advice you can trust.
In context: As sickening as it is to admit, data breaches have become a fact of life. We cannot go more than a month without one company or another announcing that a hacker or poor security hygiene left its clients exposed. As annoying as that is, it's even more irritating when the company tries to hide the intrusion.
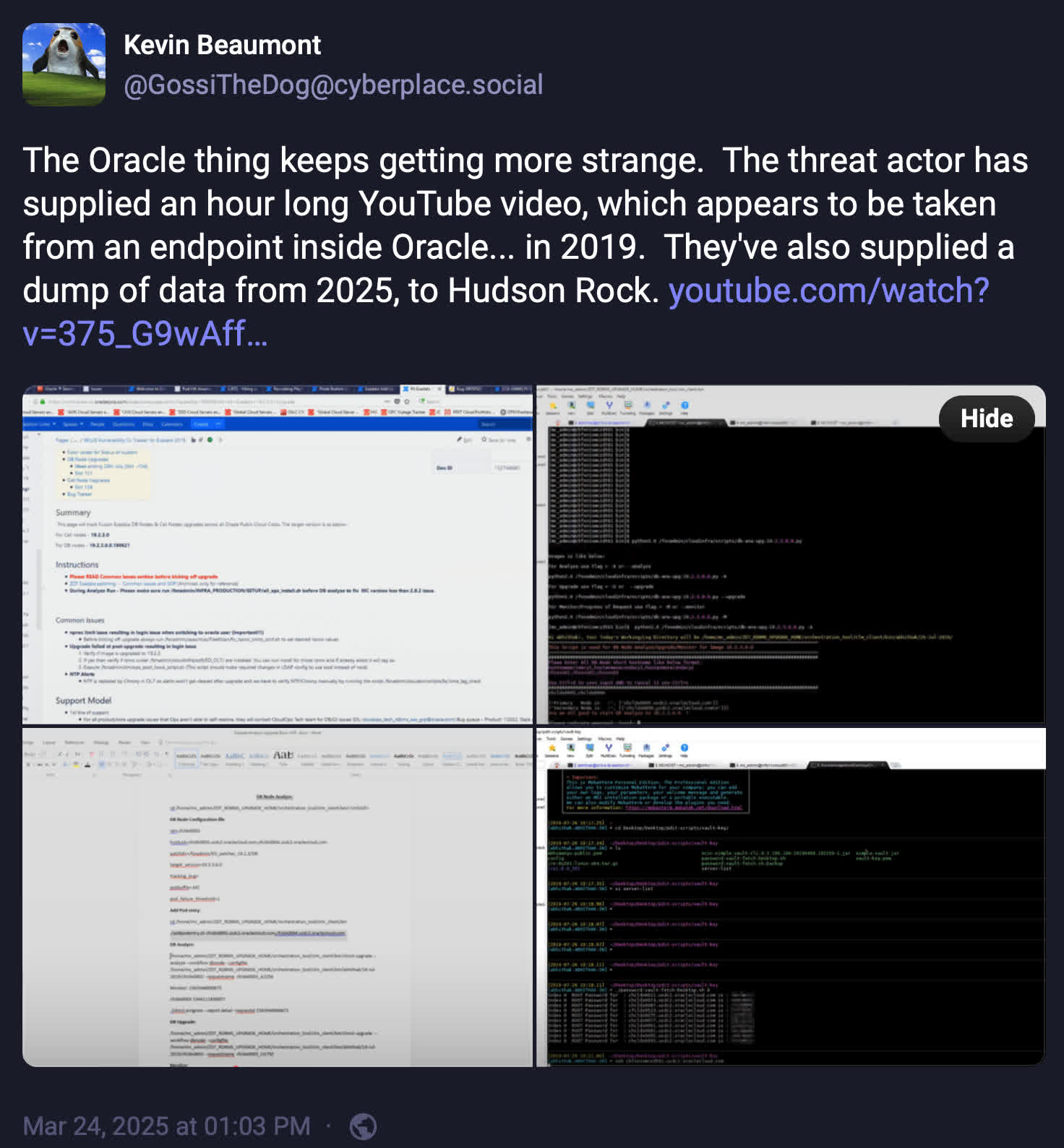
Earlier this month, a threat actor going by Rose87168 claimed to have breached Oracle Cloud's federated SSO servers and exfiltrated around 6 million records, affecting over 144,000 Oracle clients. The hacker provided an internal customer list and threatened to sell the data unless clients paid to remove their data from the trove, which included single sign-on credentials, Lightweight Directory Access Protocol passwords, OAuth2 keys, tenant data, and more. Rose87168 has also solicited help from the hacking community to crack the hashed passwords in trade for some of the data.
A day after the threat actor posted a small sample of the data, Oracle told Bleeping Computer there was no breach of its cloud service. Upon Oracle's denial, Rose87168 began leaking "proof" to the media and security researchers. Security group Hudson Rock and experts at CloudSEK concluded that the data and credentials are legitimate.
CloudSEK said that the hacker appears to have used a zero-day vulnerability (CVE-2021-35587) in an access manager software related to Oracle Fusion Middleware to breach Oracle Cloud systems without authentication.
"Pretty crazy Oracle just denied this leak, which has been verified independently by many cybersecurity firms," Hudson Rock CTO Alon Gal posted on LinkedIn on Monday.
Trustwave SpiderLabs also reviewed the evidence and concluded that the data was definitely from Oracle Cloud servers.
"The dataset described by the provided headers represents a highly detailed and sensitive user directory, likely extracted from a corporate Identity and Access Management system or HR-integrated directory such as Microsoft Active Directory, Oracle Identity Manager, or a similar platform," Trustwave's security advisory read.
The security firm also confirmed that the cache included personally identifiable information such as first and last names, full display names, email addresses, job titles, department numbers, telephone numbers, mobile numbers, and even home contact details. The hacker also uploaded a recording of an internal Oracle meeting.
"Such data in a leaked format poses severe cybersecurity and operational risks to the affected organization," Trustwave added.
Furthermore, cybersecurity specialist Kevin Beaumont noted that Oracle "rebadged" legacy Oracle Cloud services as "Oracle Classic." He claims that the company's careful wording in its response is a technically factual but disingenuous denial. The company appears to be attempting to situate the incident as insignificant or that it didn't leak current Oracle Cloud records. For reference, here is Oracle's statement to Bleeping Computer:
"There has been no breach of Oracle Cloud. The published credentials are not for the Oracle Cloud. No Oracle Cloud customers experienced a breach or lost any data."
Beaumont found the repetitious use of "Oracle Cloud" suspicious as if it might be setting up Oracle Classic to take the fall. However, regardless of the age of the breached servers, CloudSEK confirmed through some of its clients that the data was accurate and current. This conclusion debunks any notion that the breach was insignificant or contained outdated information.
Despite multiple researchers reporting that the data breach is seriously concerning, Oracle has remained silent since it denied the attack. Beaumont says the company's silence is irresponsible. Likewise, Gal called Oracle's lack of transparency and guidance "crazy." Lacking any advice from the company, Gal directed affected customers to CloudSEK's mitigation recommendations to minimize any potential damage from the leak.









 English (US) ·
English (US) ·