Serving tech enthusiasts for over 25 years.
TechSpot means tech analysis and advice you can trust.
Facepalm: BitLocker is a full volume encryption feature introduced by Microsoft with Windows Vista. The technology can apparently keep users' data safe thanks to AES and other advanced encryption algorithms, but it isn't safe from bugs and serious hacking attempts.
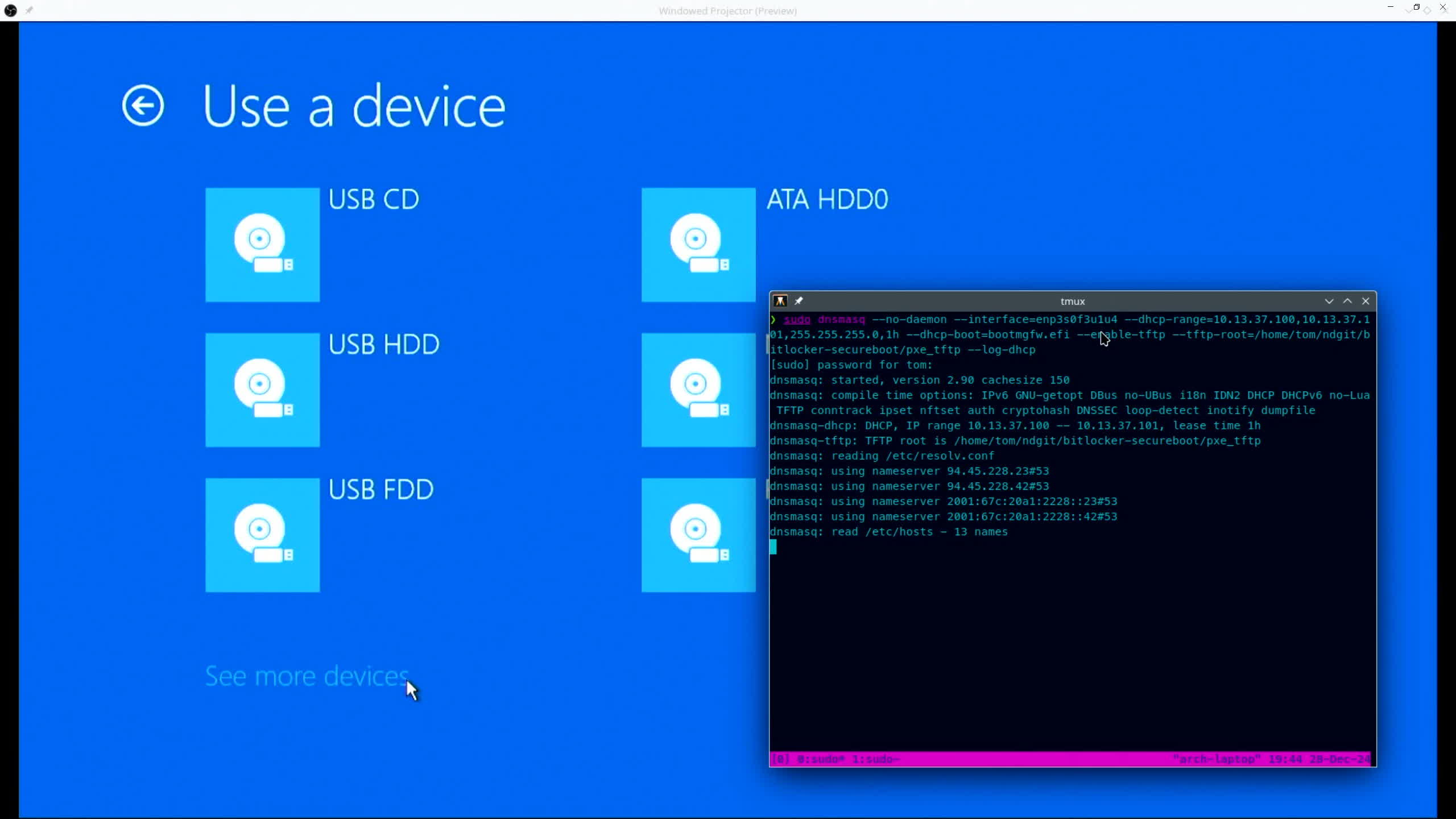
According to a presentation shown during the recently held Chaos Communication Congress at the Chaos Computer Club (CCC), Windows BitLocker can be screwed without a screwdriver. A Hacker named Thomas Lambertz found a way to exploit an old, supposedly fixed vulnerability in Microsoft's encryption tech, bypassing many security features to compromise a fully-updated Windows 11 setting.
The software vulnerability abused by Lambertz is also known as bitpixie (CVE-2023-21563). Microsoft has known about it since 2022 but never managed to effectively address the issue. The CVE-2023-21563 flaw is a "BitLocker Security Feature Bypass Vulnerability," Microsoft said. A successful attack could bypass full volume encryption and access protected data, though it would need physical access to the target system.
Lambertz was able to "repurpose" the bitpixie bug using the controversial Secure Boot technology to load an outdated Windows bootloader. The bootloader is instrumental for extracting the encryption key into memory, which can then be retrieved by using a Linux OS. The hack requires a one-time physical access to the target system, plus a working network connection.
The new bitpixie attack sounds impractical from a consumer standpoint, but the enterprise sector is a completely different matter. Many corporate clients use BitLocker to secure their PC fleets, Lambertz noted, and the encryption technology is now being enabled by default on newer Windows 11 installations. The popular "Device Encryption" mode doesn't need an additional password, which means users can "unseal" a BitLocker volume by just booting Windows with their normal user accounts.
This BitLocker configuration has been broken for a while, the hacker said, and can be attacked from both hardware and software sides to decrypt a drive's data. In his hour-long presentation, Lambertz explained how Secure Boot and TPM work, the role of PXE boot and BCD bootloaders, what the new exploit needs to run, and more.
Lambertz's presentation is in English, and was recently uploaded on CCC's official platform for video and audio content. The CCC collective is the largest association of hackers in Europe, with 7,700 registered members who have been working tirelessly since 1981 to hack almost everyone and everything.









 English (US) ·
English (US) ·