- QUIC obfuscation is now built into Mullvad’s Android and iOS clients
- The protocol disguises WireGuard traffic, bypassing censorship
- Mullvad already released QUIC on its desktop apps in September
Mullvad VPN has taken the next step in its battle against censorship-heavy networks by bringing QUIC-based WireGuard obfuscation to its Android and iOS apps.
The feature, which first rolled out on Mullvad’s desktop apps last September, now ships with version 2025.8 and newer of the mobile clients. It tunnels WireGuard traffic through the QUIC transport layer, making the connection look like ordinary HTTPS traffic, dramatically reducing the chance of a firewall block.
The move comes as part of Mullvad’s broader strategy to retire OpenVPN and focus exclusively on WireGuard-based solutions, a shift announced earlier this year.
By extending QUIC to mobile, Mullvad ensures its users get the same level of stealth and performance whether they’re at home, on the go, or traveling through a country with aggressive internet filtering.
Mullvad’s update reinforces its reputation as a privacy-first Virtual Private Network (VPN), which, much like the very best VPN services, continues to invest in cutting-edge protocols in order to stay a step ahead of censorship tactics.
What is QUIC and why does it matter?
QUIC (Quick UDP Internet Connections) is a modern transport protocol originally designed for HTTP/3. It replaces the traditional TCP handshake with a more streamlined UDP-based exchange, delivering lower latency and built-in multiplexing. The latter refers to the software's ability to carry multiple independent data streams over a single connection.
In practical terms, QUIC lets web pages, video calls, and file downloads travel together over one fast, encrypted tunnel, reducing the overhead of opening separate connections for each activity.
We are pleased to announce that our latest obfuscation feature, QUIC, aimed at helping users bypass firewalls and censorship, is now available on Android and iOS.Read more here: https://t.co/wTN01vy1RsOctober 20, 2025
Mullvad leverages QUIC through the MASQUE standard, encapsulating WireGuard’s UDP packets inside a HTTP/3 stream.
The result is traffic that appears indistinguishable from ordinary encrypted web traffic, thwarting deep-packet inspection tools that target VPN signatures.
Simply put, QUIC gives Mullvad a powerful threefold edge against online censorship.
Not only does its cloaking of VPN traffic as ordinary HTTPS make it difficult for firewalls to spot and block it, but its UDP-based handshake and low-latency design also keep connections fast. Built-in congestion control allows the tunnel to stay stable when the network fluctuates.
Together, these traits let Mullvad subscribers slip past restrictive filters without having to sacrifice performance or reliability in the process.
How to enable QUIC on your mobile device
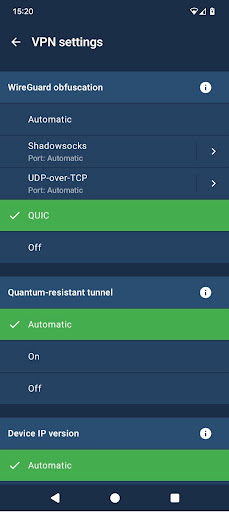
To take advantage of QUIC obfuscation, Mullvad mobile users must be using at least version 2025.8 of its iOS and Android VPN.
The apps will automatically attempt a QUIC connection after a few failed standard attempts.
Yet, if you prefer to always use QUIC, you can do so by navigating to Settings → VPN Settings → Wireguard obfuscation → QUIC and toggling the option on.
Once enabled, Mullvad automatically routes all WireGuard packets through a QUIC stream, presenting them as normal HTTPS traffic to any intervening firewall.
With QUIC now native to mobile clients, Mullvad provides privacy-focused users with the same fast, stealthy experience on the go as they already enjoy on the Windows and Mac VPN apps.









 English (US) ·
English (US) ·