There’s a new tool available for folk who want to disable Windows Defender without replacing it with a rival antivirus (AV) product. Developer and reverse engineer es3n1n released the new Defendnot tool recently. The software taps into an undocumented Windows Security Center (WSC) API to tell the OS there’s some other antivirus software turned on, thus gracefully giving Windows Defender the elbow.
In a blog post discussing Defendnot development, es3n1n introduces the new tool by highlighting how it is a replacement for their no-defender tool from a year ago. Defendnot’s ancestor disabled Windows Defender by reusing third party code from an existing AV product. Not surprisingly, it was hit by a DCMA takedown request… Defendnot started as an attempt to create a “clean implementation” of the prior project, without any ‘donor’ AV. This wasn’t easy, as WSC isn’t (publicly) documented.
Leaning on prior experience, es3n1n correctly guessed how WSC validated calls made by genuine AV products. So, they injected code into this process, with immediately promising results. The blog shows a “fresh-new antivirus I registered,” and you can see it is arbitrarily named ‘hi2.’ In the screenshot below, from GitHub, you can also see it dubbed 'hello readme:).'
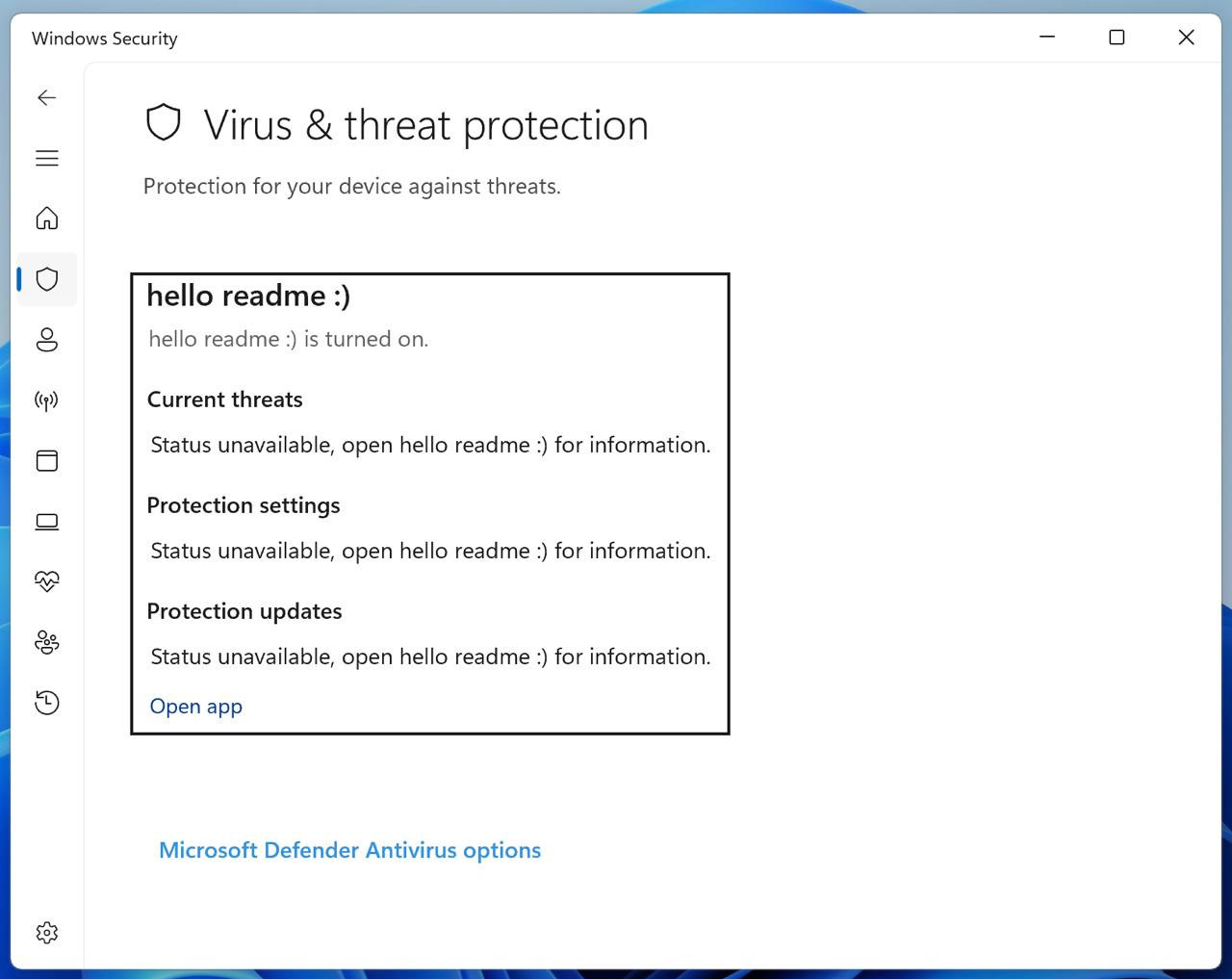
Many shenanigans later (about three days) es3n1n finessed their Defendnot tool by injecting the fake AV DLL into the already signed and trusted Windows Task Manager process (Taskmgr.exe). From there it can register the fake AV tool with any name. If you check Bleeping Computer, their reporter made a fake AV dubbed the BleepingComputer Antivirus, using Defendnot, for even more fun.
With Defendnot injected and registered, Microsoft Defender will immediately shut itself down. As your Defendnot app isn’t actually an AV program, that will leave you exposed to viruses and similar malware, as you won't have a real-time scanner enabled. To keep your new ‘AV’ and WSC implications live between reboots, Defendnot is added to Windows autorun.
Microsoft classifies Defendnot as a Trojan
It is kind of scary how a legitimate AV program can be spoofed like this, but as a ‘research project’ it forewarns OS makers like Microsoft of potential vulnerabilities which may be exploited by bad actors. If you were to download the Defendnot tool today, Microsoft’s Defender has already started to detect and quarantine it as a Trojan based on its machine learning algorithms.
Follow Tom's Hardware on Google News to get our up-to-date news, analysis, and reviews in your feeds. Make sure to click the Follow button.

 6 months ago
163
6 months ago
163







 English (US) ·
English (US) ·